AntiDDoS Protection RioRey: Service Statistics
Last Update 1/7/2025
Introduction
An AntiDDoS protection service safeguards network traffic from DDoS attacks, and at MasterDC, we provide protection based on multi-layered traffic analysis. Customers using MasterDC’s AntiDDoS protection service can also access detailed information about filtered attacks via the Customer Administration portal.
About the Tool
At MasterDC, we use the RioRey tool to defend against DDoS attacks, as it detects and mitigates threats using sophisticated algorithms designed to identify various types of attacks.
The tool operates 25 different algorithms, each containing its own subgroups to detect specific types of attacks. This ensures comprehensive protection of the network against a wide range of threats. When an attack is identified within the traffic, it is automatically blocked and prevented from reaching the network.
Service Statistics
- Log in to your account via Customer Administration.
- On the left-hand side menu, select Network Services.
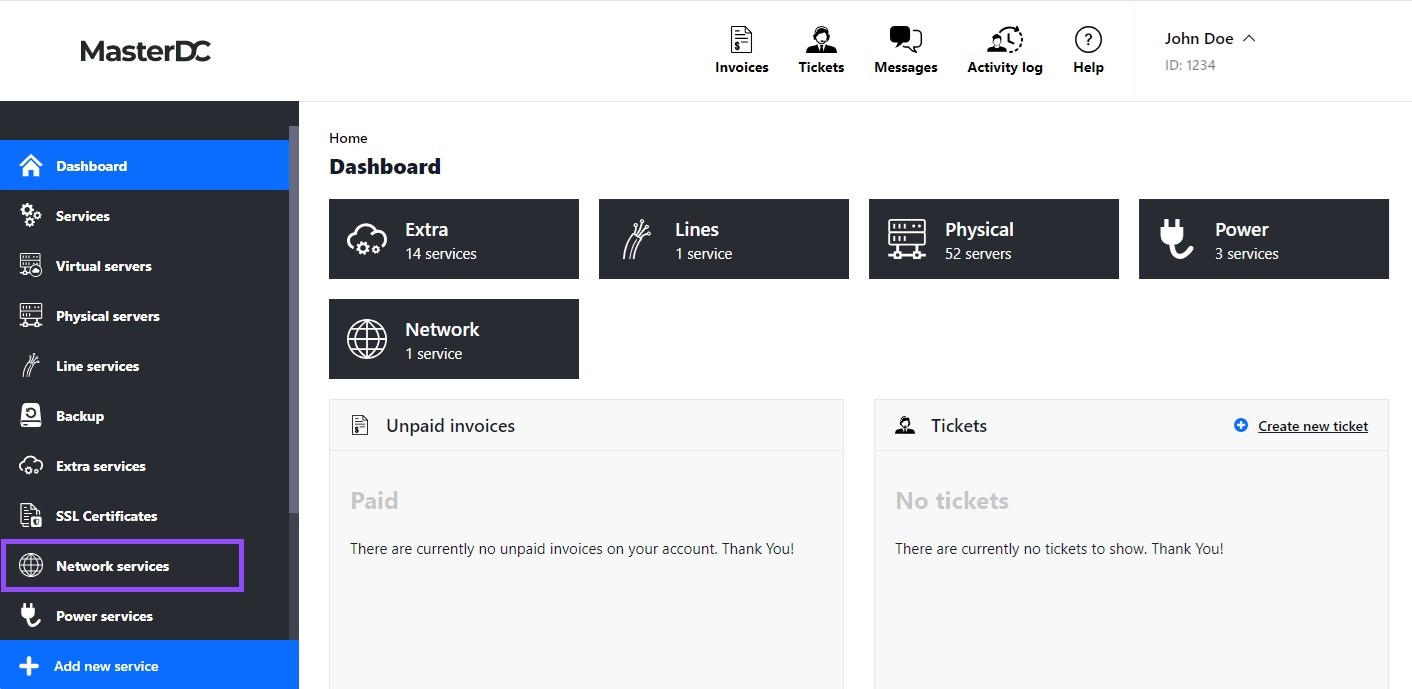
- From the list of services, choose AntiDDoS Protection RioRey. You will then be redirected to the service details page, where you can view information about the service and payment details.
- In the Attacks, Traffic, and Traffic graphs tabs, you can view information on filtered traffic in detail.
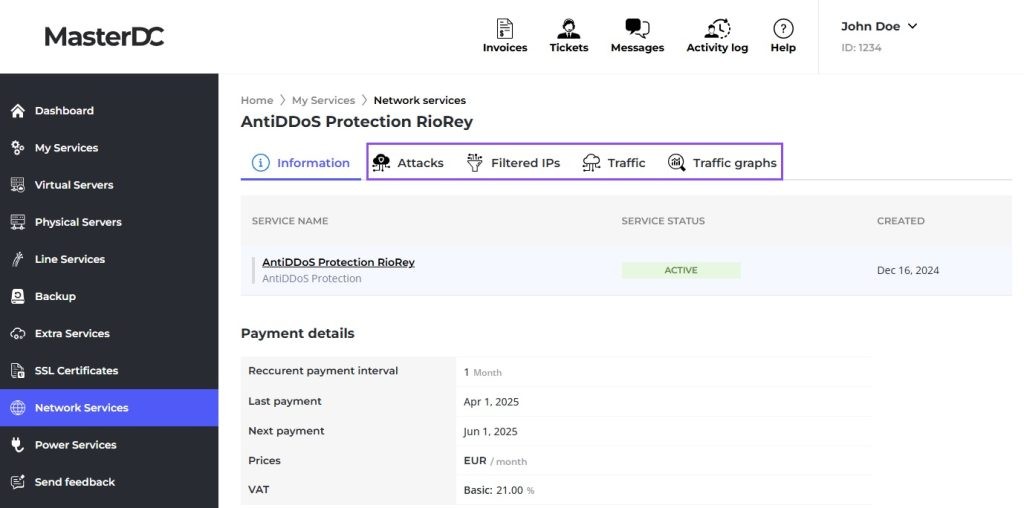
Attacks
In the Attacks tab, you will find a record of all filtered attacks, along with detailed information for each one.
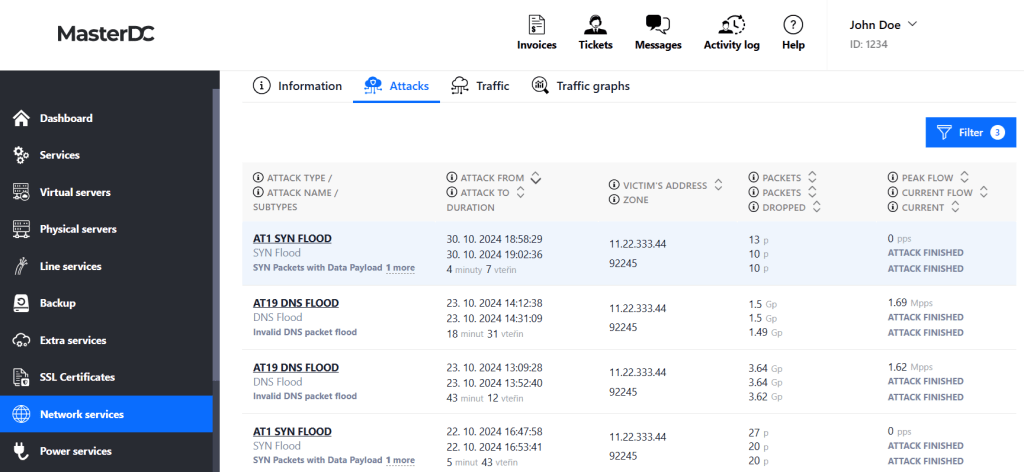
You can customise the list of both past and ongoing attacks using the filter options:
- Filter From – Select a date and time to define the start of the period you want to display.
- Filter To – Select a date and time to define the end of the period you want to display.
- Show Low-Threshold Attacks – A checkbox to show or hide less significant attacks.
Attack Details
The list of filtered attacks will include:
- Type (of attack) – A number representing the type of attack, along with a description.
- Name (of attack) – A description of the attack.
- Subtypes (of attack) – An array of strings representing the detected attack’s subtypes.
- Start – The time the attack began.
- End – The time the attack ended; if the attack is ongoing, this will be represented by the string “Infinity”.
- Duration – The total length of the attack.
- Target IP of the Attack – The IP address of the attack victim.
- Zone – The AntiDDoS service and its associated target IP; the name corresponds to the service ID within MasterDC’s system.
- Analysed (packets analysed) – The number of packets processed by the algorithm since the attack began.
- Attack Packets – The number of packets identified by the algorithm as malicious.
- Dropped (dropped packets) – The number of packets discarded by the algorithm.
- Maximum Rate (of packets) – The highest observed packet rate during the entire attack.
- Current Rate (of packets) – The current number of packets per second during the attack.
- Current Throughput – The current number of bits transmitted per second during the attack.
After clicking on a specific attack, the Attack Details will be displayed, which additionally includes:
- Victim ID – A unique identifier for the victim, corresponding to the ID used for the source of the attack.
- Analysed Throughput – The total number of bits processed by the algorithm since the attack began.
- Attack Data – The number of bits identified by the algorithm as malicious.
- Dropped Data – The number of bits discarded by the algorithm.
- Maximum Throughput – The highest observed packet rate throughout the attack.
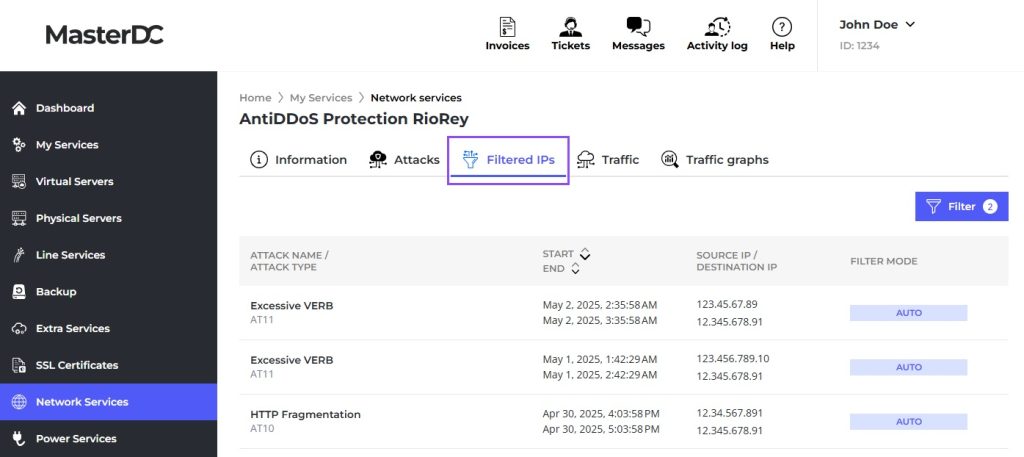
Filtered IPs
The Filtered IPs tab provides an overview of source and destination IP addresses involved in various types of attacks. The Start and End times indicate the period during which traffic from the source IP to the destination was completely blocked
Traffic
In the Traffic tab, you will find traffic logs recorded in thirty-second intervals, including all details, specifically:
- Datetime – the time of the traffic data
- Analysed packets – The number of packets that were dropped for algorithmic sampling purposes. This is separate from ‘Dropped packets’, which are solely due to drop decisions made by algorithms in filter mode.
- Input packets – The number of packets received that were destined for this zone.
- Output packets – The number of packets forwarded that were destined for this zone.
- Monitored packets – The number of packets that were detected as attacks due to their algorithms being in monitor mode.
- Attack packets – The number of packets that were detected as attacks. This number reflects packets that were both dropped due to attacks and packets that were still forwarded due to their algorithms being in monitor mode.
- Clean packets – The number of clean (non-attack) packets received that were destined for this zone.
- Dropped packets – The number of packets that were dropped due to decisions made by algorithms in filter mode.
- Input data – The number of bits received that were destined for this zone.
- Output data – The number of bits forwarded that were destined for this zone.
- Monitored data – The number of bits that were detected as attacks due to their algorithms being in monitor mode.
- Attack data – The number of bits that were detected as attacks. This number reflects bits that were both dropped due to attacks and bits that were still forwarded due to their algorithms being in monitor mode.
- Clean data – The number of clean (non-attack) bits received that were destined for this zone.
- Dropped data – The number of bits that were dropped due to decisions made by algorithms in filter mode.
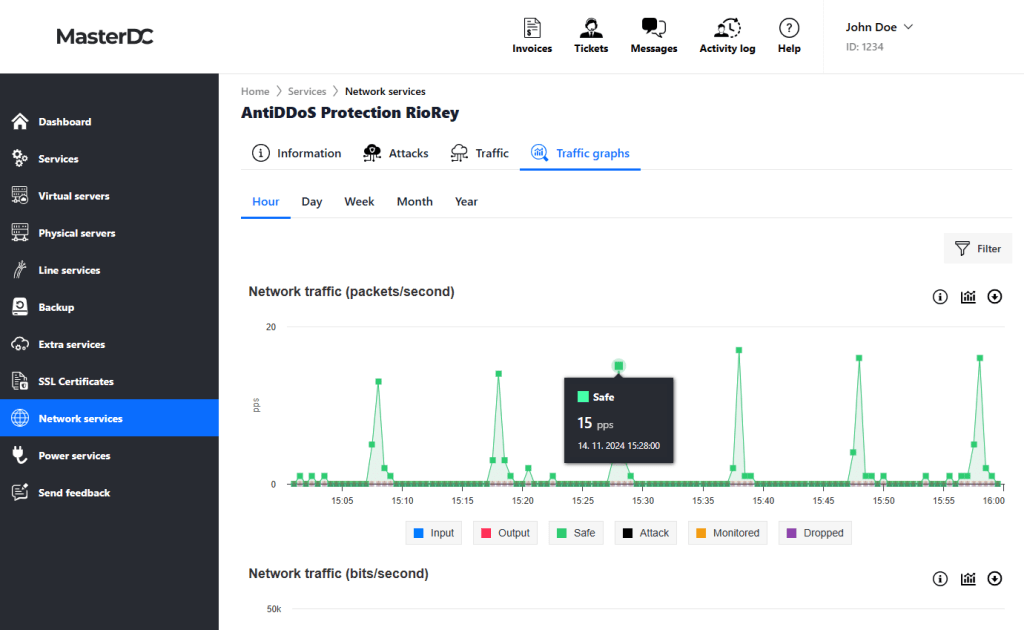
Traffic Graphs
In the final Traffic graphs tab, you will find a concise graphical representation of network traffic – packets per second, bits per second, and bits per packet. In each graph, you can easily show or hide specific data types and select the desired time period (hour, day, week, month, or year). Graphs can be downloaded in PNG, JPEG, PDF, or SVG format.
Types Of Attacks
The RioRey tool identifies a total of 25 types of DDoS attacks. A detailed taxonomy, including descriptions of all 25 attack types classified by RioRey, is available on their official website.
Email Reports
The AntiDDoS protection service also sends email reports about specific attacks. These reports are generated whenever an attack exceeds the limits set by MasterDC and are sent from the address ddos-report@master.cz. Below, you will find a description of the individual items included in the email report.
| Item Name | Description |
| DDoS Attack Summary | Basic information about the attack. |
| Group | Customer ID, e.g., 1234 |
| Zone | Zone name within the MasterDC network. |
| Reported at | Date and time of report generation. |
| Note | The attack values that exceeded the set limits and triggered the generation of the report are always indicated in bold. |
| Victim | Information about victim. |
| ID | Unique ID for the specific attack. |
| IP Address | Target IP address. |
| Attack Type | Starts with a label such as “AT8”, followed by the attack name (for descriptions of attack types, refer to the “Types Of Attacks” section in this guide). |
| Filter Mode | Attack filtering modes – there are three modes: Auto – The algorithm operates based on the current settings and automatically blocks an attack if detected. Monitor – The algorithm operates according to current settings, detecting and logging ongoing attacks but not blocking the traffic. Off – The algorithm is disabled in this mode and does not analyse traffic. If all algorithms are set to “off”, all traffic is automatically forwarded. |
| Start Time | The date and time the attack started. |
| Duration | The total duration of the attack. |
| Attack Packets | The number of attack packets. |
| Attack Bits | The number of attack bits. |
| Dropped Packets | The number of dropped packets. |
| Dropped Bits | The number of dropped bits. |
| Avg. Attack Rate pps | The average attack rate (packets per second). |
| Avg. Attack Rate bps | The average attack rate (bits per second). |
| Peak Attack Rate pps | The peak attack rate (packets per second). |
| Peak Attack Rate bps | The peak attack rate (bits per second). |
| Attack Subtype | Information about the attack subtype. |
| Attack Type | The primary type of attack (as listed in the “Types Of Attacks” section of this guide). |
| Attack Subtype | The numerical designation of the attack subtype. |
| Description | A description of the attack subtype, typically including details about the size and speed of data sessions. |
| Attackers in Filter List | Information about the attackers. |
| Attacker IP Address | The source IP addresses of the attackers. |