The audit basis is through a detailed, in-depth system analysis utilising specialised non-invasive software, revealing vulnerabilities and errors in the configurations.
How do we improve the security of your operating system?
OS software analysis
Manual scanning
We complement the in-depth software analysis with a manual check from the perspective of an experienced sysadmin. The main focus is on the OS’s key parts and critical components.
Report and recommendations
You will receive the testing outcome in a clear report. However, the number of software analysis recommendations typically get pretty high. Therefore, we will help you find the most important ones for risk reduction.
Review of changes
Once the recommended measures have been implemented, we carry out a review of the applied changes. Our administrator verifies the updates and provides you with additional feedback.
Get it solve by an OS audit
Configuration errors
Operating system modifications or firewall configurations can compromise an OS’s reliability, even though they are primarily done to improve the OS’s security and functionality. However, an in-depth scan of all system components will reveal these errors.
Critical and potential vulnerabilities
The list of improvement suggestions is typically very long for complex systems. Therefore, we will highlight the system’s greatest threats so that you can address them as a priority. The audit also serves as a basis for penetration testing as well as for new threat discovery.
Compatibility checks
With Linux systems, tool compatibility can sometimes be a hassle and requires a proper setup. An operating system audit will also help discover these shortcomings as it checks the tool’s compatibility and compares it to established standards.
System hardening
We assess all web applications and operating system tools, including Docker images. In short, everything you use. Once the proposed changes have been implemented, the OS will be tuned to minimise risks.

Why get a professional OS audit?
Most operating systems and applications are managed with a focus on functionality. Therefore, security is only addressed when an attack causes system failure. However, an audit prevents such situations and thus is useful for anyone running an operating system.
- Several cybersecurity standards require an OS security audit.
- Native tools for system scanning are not detailed enough.
- It prevents the impact of potential vulnerabilities in, e.g., Apache or PHP.
- You will get security recommendations for the technical team.
Operating systems we analyse
- CentOS
- Fedora
- AlmaLinux
- RockyLinux
- RedHat Enterprise Linux
- CloudLinux
- Oracle Linux
- Debian
- Ubuntu
- Windows Server
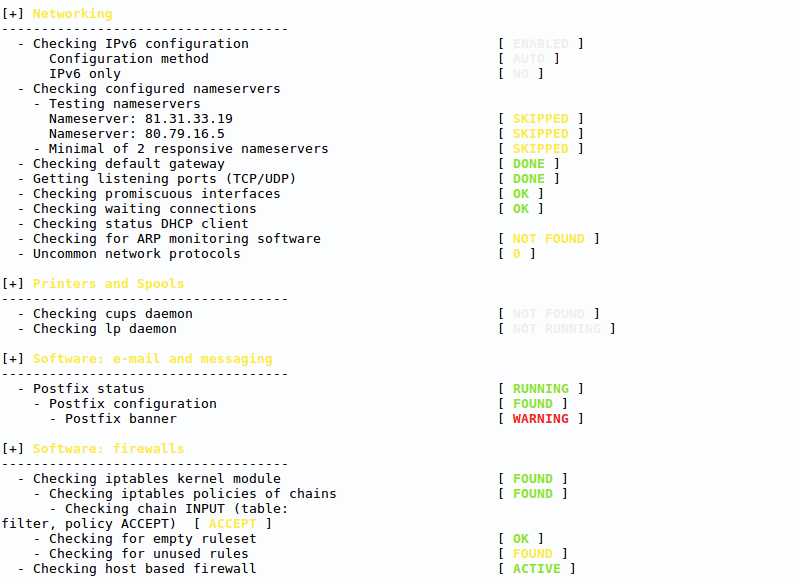
More about the used methods
We perform security audits using a combination of automated tools and manual verification. Depending on the environment, we either use non-invasive analytical software or temporarily install an agent to collect more detailed data. The analysis includes a review of system components, configuration settings, and potential vulnerabilities, complemented by manual checks of selected parameters. The final output is a well-structured report outlining identified issues and recommended actions. Once the recommended changes have been applied, we carry out a follow-up check and update the report accordingly.



