How to secure your server: 5 tips for the best server protection
Server protection is one of the biggest concerns for security teams nowadays. Weak protection can open the door for attackers to gain unauthorized access to your server through several types of malware. Today cybercriminals are more aggressive than ever. Set up your server protection with these basic steps to keep attackers away.

SSH keys: a must for server protection
Also known as Secure Shell, the SSH keys are a cryptographic network protocol. The SSH keys provide a higher level of security than a conventional password.
This is because the SSH keys can resist a brute force attack much better. Why? because it is almost impossible to decipher. On the contrary, an ordinary password can be cracked at any time.
When SSH keys are generated, two types of keys are obtained: a private one and a public one. The private one is saved by the administrator while the public one can be shared with other users.
Unlike traditional passwords on servers, the SSH keys have a long string of bits or characters. To crack them, the attacker would take some time trying to decrypt access trying different combinations. This happens because the keys (public and private) must match to unlock the system.
Set up a Firewall
Having a Firewall is one of the basic measures to guarantee server protection. A Firewall is necessary because it controls incoming and outgoing traffic based on a series of security parameters.
These security parameters are applied according to the type of Firewall you use. There are three types of Firewall according to their technology: packet filter firewall, proxy filter, and a stateful firewall. Each of these services offers a different way to access the server.
For instance, a filtered Firewall is one of the simplest mechanisms for server protection. It basically checks the IP address, the port source, destination IP address, destination port, and the type of protocol: IP, TCP, UDP, ICMP. Then compares this information with the specified access parameters and if they match, access to the server is allowed.
A proxy filter is placed as an intermediary between two communicating parties. As an example, we can think of a client computer that requests access to a website. The client must create a session with the proxy server to authenticate and validate the user’s access to the internet before creating a second session to access the website.
Regarding a stateful Firewall, it combines the technology of a proxy and a packet filter. In fact, it is the Firewall most used for server protection since it allows to apply security rules using UFC firewall, nftables, and CSF firewall.
In conclusion, using a Firewall as a server protection tool would help you defend the content, validate access, and control incoming and outgoing traffic through pre-established security parameters.
Establish a VPN
Setting up a VPN (a virtual private network) is essential to access the information of remote servers under the security parameters of a private network.In basic terms, a VPN behaves like a virtual cable between a computer and a server.
This virtual cable creates a tunnel through which encrypted information travels. In this way, the information exchanged between the server and the authorized computer is protected from any intrusion.
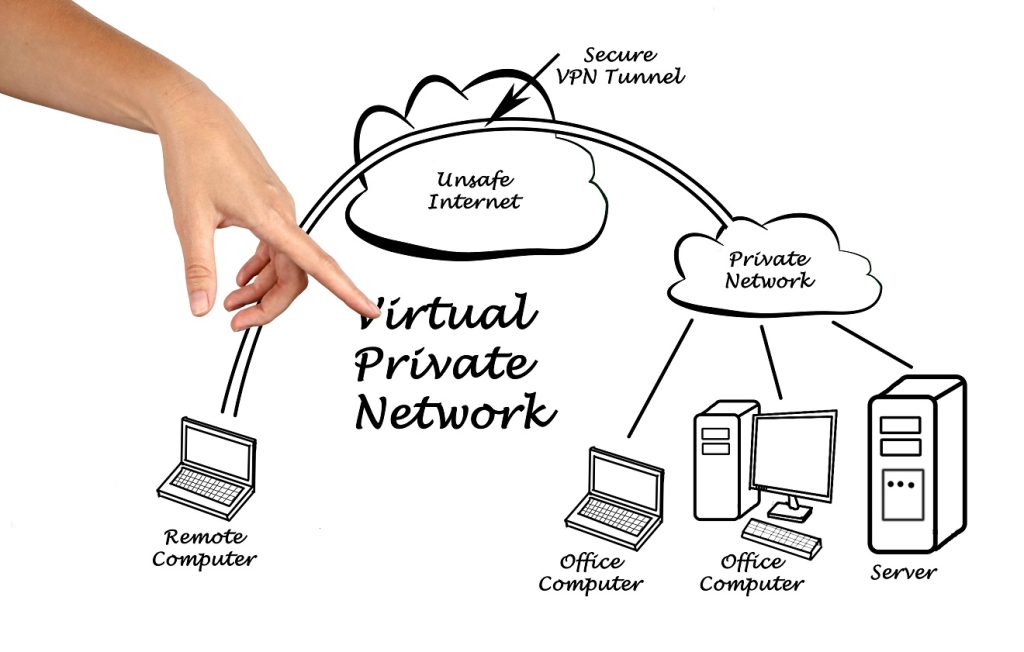
A VPN to create secure protocols to filter the outbound and inbound data
The server protection is reinforced by a VPN since it controls access to specific ports through a private network. This means that public access to the server remains blocked and only users with access to the private network can exchange information with the server.
Learn more: IP address, how does it works and five tools to browse anonymously
In conclusion, a VPN offers security protocols that protect the information that passes through the server and create secure connections through the encryption of data.
Encryption using SSL and TLS
SSL and TSL encryption are an alternative if you do not want to use a VPN tunnel. The SSL (Secure Sockets Layer) is a digital certificate to protect the information transfer.
On the other hand, TSL (Transport Layer Security) is the second generation that follows SSL. The TLS establishes a secure environment between the user and the server to exchange information. It does this by using HTTP, POP3, IMAP, SMTP, NNTP and SSH protocols.
When using SSL and TSL through a KPI (Public Key Infrastructure), you can create, manage, and validate certificates. You can also identify systems with specific users to encrypt communication.
In other words, when you establish authorization certificates, you can trace the identity of each user connected to your private network and encrypt their traffic to prevent the communication from being hacked and strength your server protection.
Don’t miss it: Dedicated or managed server? what you need to consider before choosing one of them.
Don't forget the Isolated Execution!
An Isolated Execution is a way to protect your private network from massive malware infection. Isolated Execution works by creating an isolated environment for the execution of unknown or untrusted applications.
This way you can open suspicious files from unknown sources without compromising the rest of the infrastructure. To imagine this, think about what happens in science fiction movies.
A group of scientists is examining an extraterrestrial creature inside a sealed chamber. This measure prevents the spread of unknown viruses that can kill humans. Maybe our example is exaggerated but it is exactly what Isolated Execution does to protect your infrastructure.
The Isolated Execution acts through “sandboxes”, as the controlled environments are called. You just need to select the file and send it to an isolated execution using the option “Send to Sandbox VM”.
If the file is infected, it will only affect the environment of the Sandbox and it will be deleted after the Sandbox is restarted.
Some advantages of an Isolated Execution are better detection of threats, delay an attack by limiting the speed of propagation and distribution of exploits, and avoid a human error when executing files in vulnerable environments.



