FortiGate, pfSense and MikroTik: How Firewalls Work and Which One to Choose
The choice of the right firewall might be really tough; it depends on how you need to filter the traffic and what your security requirements are. To make it easier for you, we jotted down how the firewalls work, including the differences between pfSense, MikroTik and FortiGate solutions which are all provided by the MasterDC. We also got together some practical advice on what to be careful about when making the choice.

Firewall is an inseparable part both of company IT and personal computers. It is useful at any internet communication involving two networks with different level of security and reliability. Firewalls separate those safely and facilitates filtration of all the traffic flowing into the secured network.
When filtering, a check on traffic is conducted and the decision whether to let it into a protected network is made. It is just the means by which individual firewalls decide on non/safety of certain traffic that draws the line between them.
A reference model of seven-level architecture might come in handy when illustrating computer and telecommunication networks. Each level has its functions necessary for communication clearly defined. Firewalls differ from each other particularly in the level on which the traffic is filtered.
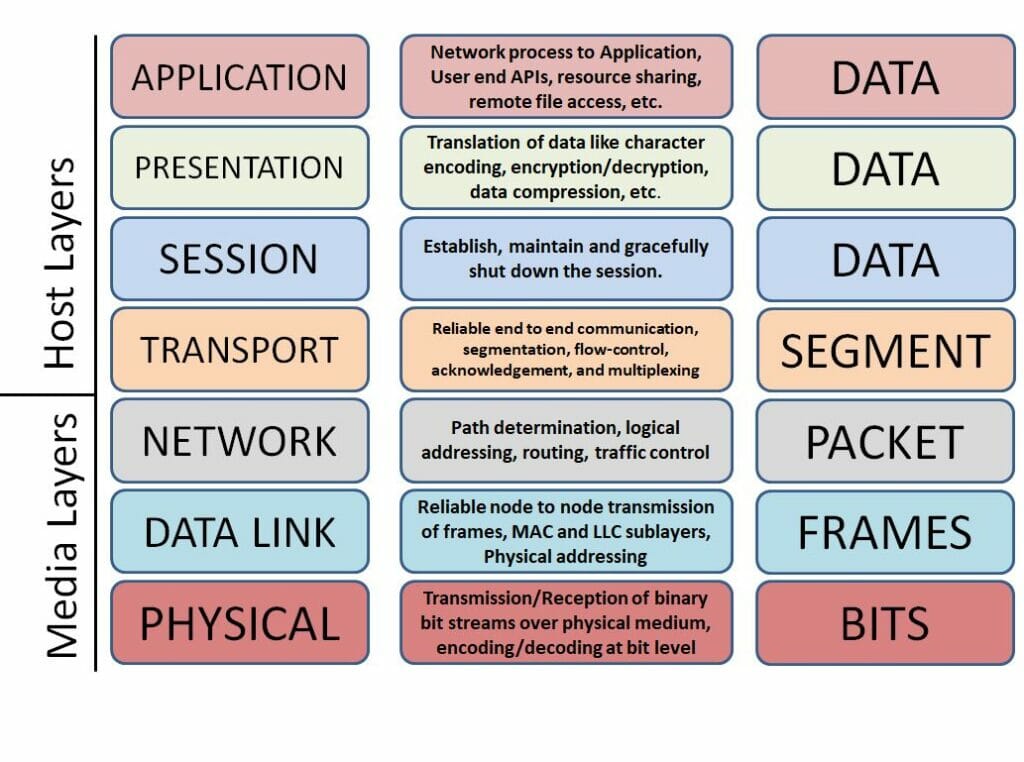
Reference model ISO/OSI, an illustration of communication solution in computer and telecommunication networks using multi-level model. Source: networkhope.in
Firewalls Based on the Ways of Traffic Filtration
Older firewall versions control solely traffic source and its target. Target IP addresses and ports are controlled on the network level. Firewall thus blocks the traffic based on the fact from which node and/or network it is coming from.
Nonetheless, data for transfer are segmented into smaller parts, so-called packets, of which each and every one bears in itself only a piece of information about the character of the data. Hence a complete message is assembled in the final destination, i.e. on the receiver’s part; that is why the firewall investigating only the control information (otherwise source and target) can hardly discover whether or not does the message contain any threats. Another problem is the fact that origin of the packet might be falsified easily. In order for the firewall to recognise a harmful packet content, it must be able to search for the associations between individual packets.
Donno What to Choose?
Nechte to na nás. V nabídce MasterDC máme firewally se základními i pokročilými funkcemi. S výběrem řešení či jejich kombinací vám poradíme a připravíme jej přímo pro váš server nebo interní firemní síť.
More advanced firewalls, i.e. the second generation of firewalls, inspect packets on transport layers and keep track of the connection state (stateful inspection) unless they gain sufficient amount of information. Second generation firewalls are able to recognise whether the incoming packet is a part of an existing connection or the beginning of the new one. It is not exceptional though that the packet is not involved in any connection. Some of DoS (Denial of Service) attacks strategically increase the number of individually incoming packets in order to overload the firewall.
So as to reveal the attack, the DoS must approach all other packets with awareness of the previous attack; it must, in a way, ‘remember’ its state which is why these firewalls are well-known as ‘stateful firewalls’. However, fundamental transfer mechanisms are arranged independently, regardless the processing of the previous request, which is the reason why the context between packets disappears.
Hidden threats are most efficiently revealed in the application layer, in which the packets might be inspected in more detail, i.e. not only where they are coming from, but also where they are aiming to and what the character of the data, they are transferring, is. Firewall that inspects the packet in the application layer works in the application gate (proxy) and is able to estimate whether the packet is attempting to bypass the gate using protocol on the allowed port or whether it uses protocol for wrong purposes. The above mentioned solution is far more demanding on the hardware though, has higher latency and requests are processed slower.
The most sophisticated firewalls are assigned as the next-generation firewalls. They combine the above mentioned functions and, furthermore, they also implement the so-called ‘deep inspection’. These firewalls thus, in comparison with stateful and application firewalls, inspect the whole packet and its content in very much detail, and thus represent an efficient protection against malware attacks and other external threats. A precise list of functions in these devices does not actually exist since it is an advanced and flexible commercial solution.
| Pros | Cons | Protection level | |
|---|---|---|---|
| Packet firewalls | Low performance, low price and fast filtration. | Surface control, does not control the application layer and protocols, does not authenticate the user. | Higher vulnerability – does not check data contained in packets. |
| Stateful firewalls | They control the entire connection, including the data contained in the packets. | They do not authenticate users and may be subject to DoS attacks. | They provide a standard level of protection. |
| Application firewalls | Networks completely separate and ensure the anonymity of the user. They are not subject to geolocation restrictions. | They are not compatible with all network protocols, require additional configuration, and can adversely affect performance. | If configured right, they provide high web app and server protection. |
| Next-generation firewalls | In-depth packet analysis, spam filtering and control of individual applications. | Higher price, require configuration for proper functionality. We recommend using a specialist. | They provide a very high level of protection. |
Shall I Go for a Software or Hardware Firewall?
Except for making the decision on how detailed the traffic filtration must be, you must also focus on one important question. Do you want to install the firewall on the individual devices themwelves or do you prefer to purchase a hardware variety so that the firewall sources in the internal network get separated?
Take into account that the software variety will have to utilise a certain RAM and CPU part of the device and thus might reduce its performance. If you want the firewall to protect several devices, it is necessary to implement it, configure it and update it separately. When installed on the device, the firewall can better distinguish individual programs during in/out-coming filtration procedure
If as a hardware, the firewall is separated from the internal network and, in contrast to software, has its own sources. It filters data which leave and come into the internal network, not the data flowing among the devices involved in the network. For vast IT infrastructures and networks, a hardware firewall is particularly convenient. The configuration and maintenance is conducted in one place, but at the same time requires, to some extent, professional knowledge.
MikroTik: Stateful Firewall as Hardware
MikroTik company develops so-called RouterOS that involves firewall as well. It has its own RouterBOARD that might be utilised as an active network element. An efficient router with RouterOS (based on Linux) supports, except for routing, a VPN server (Virtual Private Network) and the above mentioned firewall.
RouterOS firewall belongs to the category of stateful firewalls hence it can reveal packets that are not involved in the connection and are not reliable. MikroTik firewall filters IP addresses, port protocols, network interfaces, source MAC addresses and TCP options (Transmission Control Protocol).
Having its own hardware (RouterBOARD), the RouterOS guarantees high performance and stronger resistance to overload. All configuration and maintenance are thus conducted centrally via SSH, Windbox program, which copies text interface, or graphical interface available via web browser.
PfSense: Software Stateful Firewall
Similar to RouterOS firewall, a stateful firewall open source pfSense software filters the traffic. PfSense, the same as MikroTik, remembers the information about previously controlled connections, which is why it is able to check other packets easier and faster. Data are stored in the chart of states that involves for instance the source, protocol, and port number, which is sufficient for the specific connection identification in question.
However, it is not just firewall that pfSense works with; as with the RouterBOARD, it can work as LAN, WAN and/or VPN router, hotspot or DNS server. It can be in hand in port forwarding and Network Address Translation (NAT).
Considering software alternative, it is highly flexible and scalable. The resources for firewall operation can be gradually in/decreased as needed. Hence you run the program on the one device, but you may deploy it on the server itself and protect the network to more extent.
PfSense is based on FreeBSD, UNIX OS, which is the reason why it is compatible with those systems. Not only may it be installed on any hardware that meets the conditions of FreeBSD Hardware Notes, but also in virtual environments (VMware, KVM, and others). The system is managed simply via the user interface.
FortiGate: Next-Generation Firewall for Specific Purposes
FortiGate firewall made by Fortinet uses an artificial intelligence and machine learning for a deep packet inspection, i.e. a specialised control of more complicated protocols.
Due to automatic updates from Fortinet cloud, the firewall is able to recognise not only familiar attacks, but also the state-of-the-art viruses and other content threats of the malware hitherto unknown. Familiar attacks and harmful codes of worm type are identified before a specific device and/or network is affected, and are mitigated automatically.
Fortigate firewalls are available in hardware alternatives suitable particularly for company networks and/or interconnection of subsidiaries, since they can handle greater amounts of data-flow. For clusters and infrastructure, which must be approached physically, for instance if you have a part of your IT in Amazon Web Services or Azure, software Fortigate firewall version are available.
Except for the next-generation firewalls, the company also provides specialised application firewalls to protect web apps (Web Application Firewall) or email (Antispam filter).
| Elementary functions | MikroTik | pfSense | FotiGate |
|---|---|---|---|
| High availability | NO | YES | YES |
| Comfortable web management | NO | YES | YES |
| Zone firewall / IP filtration | NO | YES | YES |
| Network Address Translation | YES | YES | YES |
| Port forwarding | YES | YES | YES |
| Advanced functions | NO | NO | YES |
| Deep inspection | NO | NO | YES |
| Intrusion Detection and Prevention Systems (IPS/IDS) | NO | NO | YES |
| Antivirus | NO | NO | YES |
| Botnet IP Blockage / Domain | NO | NO | YES |
| Unknown malware identification | NO | NO | YES |
| Malware outbreak identification | NO | NO | YES |
| Text document control | NO | NO | YES |
| Two-factor authentication | NO | NO | YES |
What to focus on when selecting a firewall?
A final choice does not have to include solely one firewall. Different types might be combined in order to form a multilayer solution for a stronger protection. When making a decision, the size of the IT structure, for which the security solution is being chosen, is the key factor.
Firstly, consider whether you want to install software firewall on each device individually or whether to implement an independent hardware. To separate firewall in an independent hardware is more costly and you will need an expert who has gained some experience with firewall management.
We also recommend focusing on the packets-per-second and Mbps permeability. Based on this data you will choose a final hardware and software configuration. Particularly concerning greater data flow, a higher-performance hardware is necessary. Do not forget the differences between the traffic intensity in different day and night hours.
Number and type of firewall gates should reflect network security requirements. For the clients who require most from security and work with confidential data, we most often implement next-generation firewalls.
Firewalls are inherently very flexible, and with proper configuration and maintenance, non-commercial variants such as pfSense will also protect you well. Take advantage of the opportunity to combine several solutions, thanks to which you will turn your IT into an impenetrable fortress. And if you are unsure about the choice or configuration of the firewall, contact us.



